
These types of emails are not new and many of them have been around for quite some time. impersonating Apple tech support to tell us that our account has been suspended, that we must update our personal information or any other excuse, so that we introduce through a malicious link to an external website, our credentials and that in this way they can access our information.
The serious thing is that even the website to which the link takes us has a legitimate appearance with authentic links to Apple's support website with online forums ... however when you click on "My Apple ID" it redirects you to an address that has nothing to do with the authentic web.
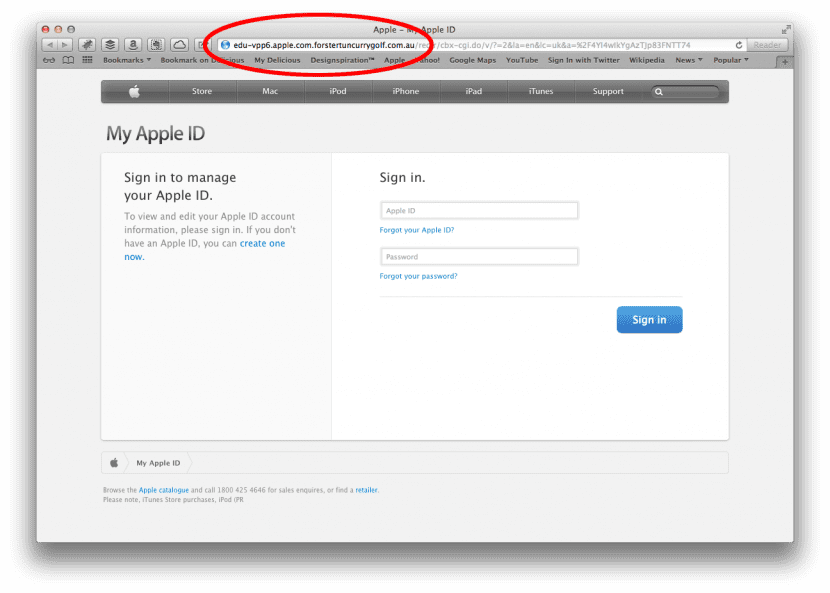
I simply return to the subject because according to some publications the attacks are increasing in number, being increasingly sophisticated in terms of the real appearance of the forged email or website and you really have to be careful not to fall into the trap.
The most effective tip is to always check the URL address bar before clicking or further researching the page. When receiving an email in most versions of the Mail application, if we hover over the external link, it will reveal the URL in a kind of pop-up rectangle. It is even better than before clicking any link, let's access the web for ourselves and we do it without being "taken".
In any case, medium or advanced users will have no problems identifying them if you stay tuned, on the contrary the casual user Those targeted by these types of attacks are much more likely to compromise your passwords. Hopefully Apple takes note and can automatically identify these types of emails to send them directly to the spam folder within the native mail application.