Since OS X 10.8 Mountain Lion was released, Apple added a security routine to prevent the execution of unauthorized programs by the user called Gatekeeper which could be configured in different security levels to control all those applications not signed by Apple or that are not trusted.
To do this, what this Gatekeeper does is show a warning that this or that program can be potentially dangerous at the time of executing it, so depending on our configuration, it will not allow us to carry out that execution, so if we use too many programs from 'unidentified' developers, it is best to activate the option with the lowest level of security.

However, if we do not want to expose security, we can also configure any of the others two levels of security although Gatekeeper will not allow us to execute anything that has not been previously signed.
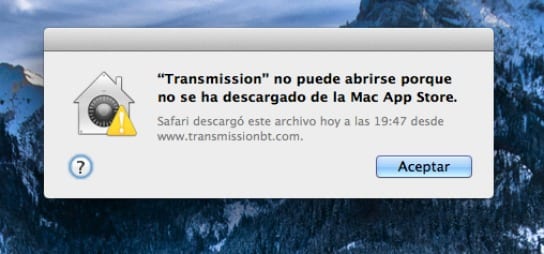
On the other hand, we can "skip" this restriction when trying to open our specific application, since we can do so via context menu with the open option, this will create an exception in the routine that will cause that when we reopen it, it will show us the "Open" button where it did not leave us before.
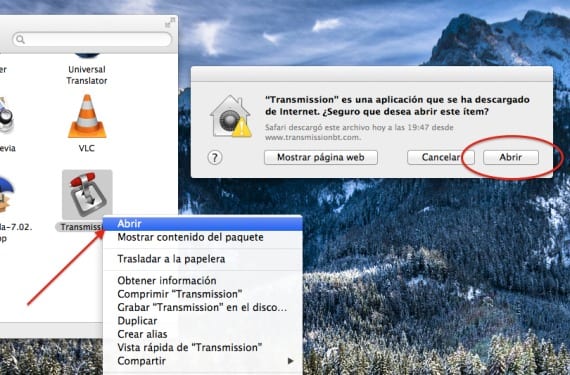
Apart from this method if we have OS X Mavericks installed it will also show us a section on how we tried to open the application and we have not been able to do so. so we can specify to Gatekeeper to open it anyway without having any kind of problem creating the same exception in the routine as if we did it from the "Open" option.

More information - Create network locations with different configurations