
Apple's computer systems, Mac OS X, are faced with a new threat that allows attackers take control of the system seamlessly and collect information from infected computers.
The security experts of Bitdefender have detected this malware known as Eleanor that affects Mac OS X systems by opening a back door and connecting the equipment through the Tor network.
Eleanor is being distributed over the network through an application called Easy Doc Converter, seemingly useful and harmless, which users install with the intention of making use of document format conversion. The interface is simple: a limited area to drag files that never get converted.
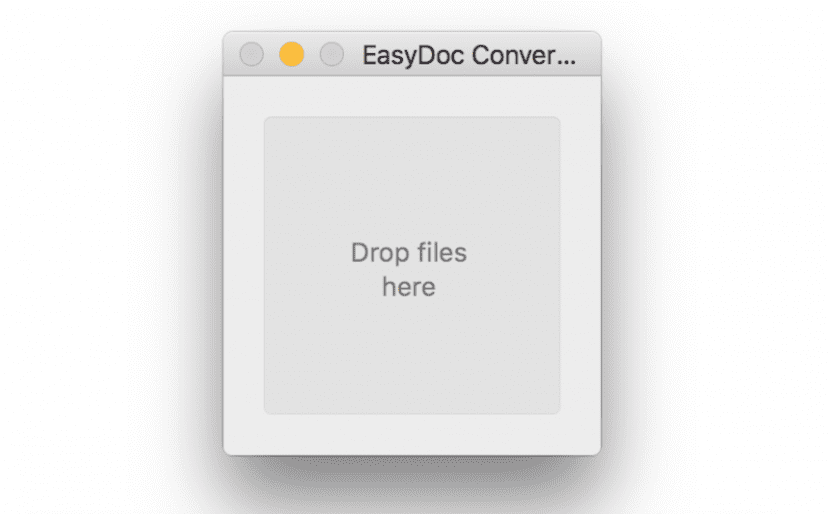
Not only will the application not convert any files, but the Bidefender experts have reported that the installation of this application includes the installation of three other components: the back door, a client of the website Pastebin or with a apache server. Tiberio Axinte, Bitdefender Technical Lead, has warned of the threat Eleanor poses to computers.
“This type of malware is particularly dangerous, as it is difficult to detect and offers the attacker full control of the compromised system. For example, they can block access to your own computer, threaten to restore your private files or turn your system into a botnet to attack other devices. The possibilities are endless."
Eleanor creates a direction Tor on infected machines, allowing attackers to connect and the full access to the entire file system, as well as capturing images and videos via the webcam.
Although Eleanor has not caused significant damage at the moment, it is known that she is capable of executing, in addition to PHP code, PERL, Python, Ruby, Java, and C language scripts. This would allow malware create, delete and edit information and system files, thus posing a very compromising threat.
At the moment we have no more information about Eleanor. However, attackers are known to be using the malicious application to upload encrypted information through the installation and used to link your computer to a botnet or network of zombie computers.
The original application has not been validated by Apple, so security researchers recommend changing the Mac security settings to allow only applications downloaded from the Mac App Store and developers identified.
