
Apple ensures the security of the content of our computers, but also the security of our computers. For many years we have been able to find our iOS device and even erase and block it if we do not have access to it. The problem arose when the equipment was turned off Either he had disconnected all kinds of wireless communication.
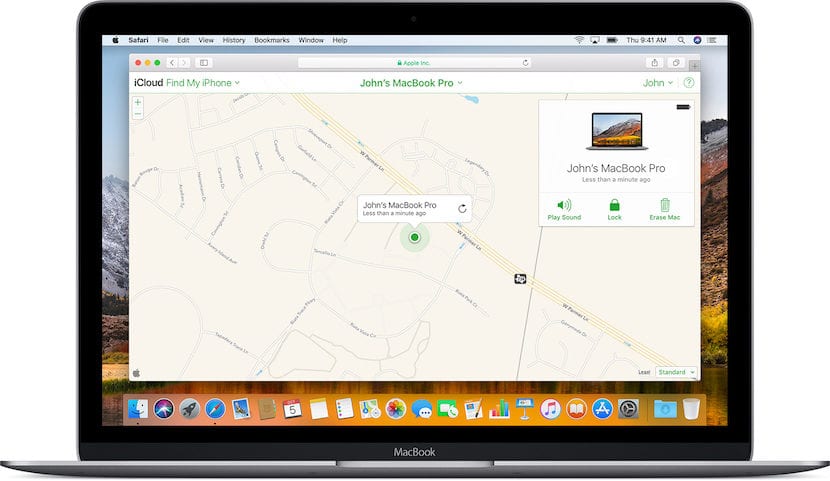
Now Apple improves this service to find even computers that are asleep. Even in sleep mode, our team can send the location when we are looking for it thanks to an improvement of Find My Mac.
The operation will be as follows. Despite being at rest, the computer will try to connect to Apple devices, able to send the location of the same. For example, if we are looking for a stolen device, it can be connected via bluetooth by with other devices connected to a network and send your position.
The idea is very good, but once again the debate will arise about data privacy and if information is sent securely. Apple ensures that this information travels fully encrypted even for the device that is reporting the location. This will only act as a transmitter and will consume the minimum of energy and data from said device.
As a complement to this measure, Apple has also launched Activation Lock. This action can be found on any computer with the T2 chip. It allows any stolen Mac to be rendered useless, that is, totally unusable. We prevent theft unless we enter our Apple ID on that device, for example, if we have managed to recover it. If you doubt whether your Mac has the T2 chip, you can consult the page Apple to that effect. In it you will know that it has this security, all Mac computers from 2018 onwards, as well as the first iMac Pro from 2017.
