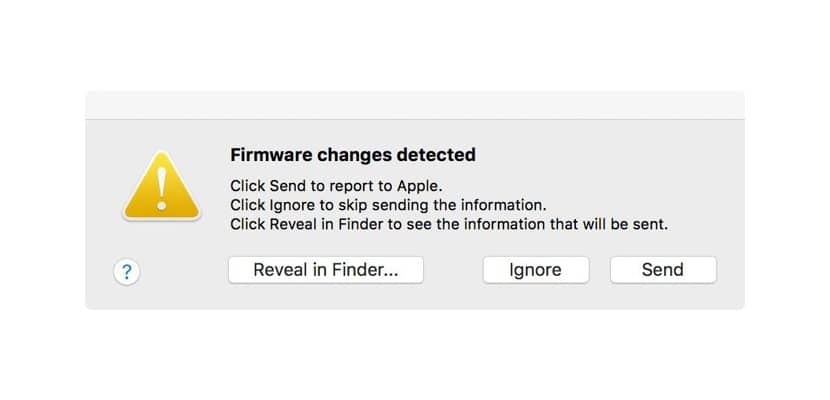
It's official now. The final version of macOS High Sierra is now available for download through the Mac App Store and little by little we are learning about new features that do not affect the performance of this new version, but rather focus on improving or perfecting the internal functioning. Before the launch of the final version of macOS High Sierra, a routine has been detected that is responsible for checking the firmware of our Mac to verify if modifications have been made that could put the security of our Mac at risk.
This routine takes care of check the Mac ID and its firmware against the data stored in the Apple database. If any modification is found during the check, the user will be invited to automatically send a report to Apple. This new feature has been designed by Apple engineers Corey Kallenberg, Xeno Kovah and Nikolaj Schlej, and made it known through tweets that have currently been removed from their respective Twitter accounts.
This report exclude data stored in NVRAM from the report and they will allow Apple to check if any problem is found on our Mac, but we don't really know what Apple will do with that data. It is also not clear to users who have modified their Mac Pro 4,1 firmware to look like Mac Pro 5,1 or those users who do Hackintosh, but everything seems to indicate that it will not do anything about it.
According to the tweets in which Xeno Kovah announced this feature, the message that he will show us about the modification will be shown only once, a message that will allow us to share the report with Apple or cancel it. Until another modification occurs, Apple will not display such a message again.
