Macs (iPhones too) with Touch ID or Face ID use a separate processor to handle your biometric information. It's called Secure EnclaveIt is basically a whole computer unto itself, and it offers a variety of security features. This is why the exploit found is so important.
What is the Secure Enclave?
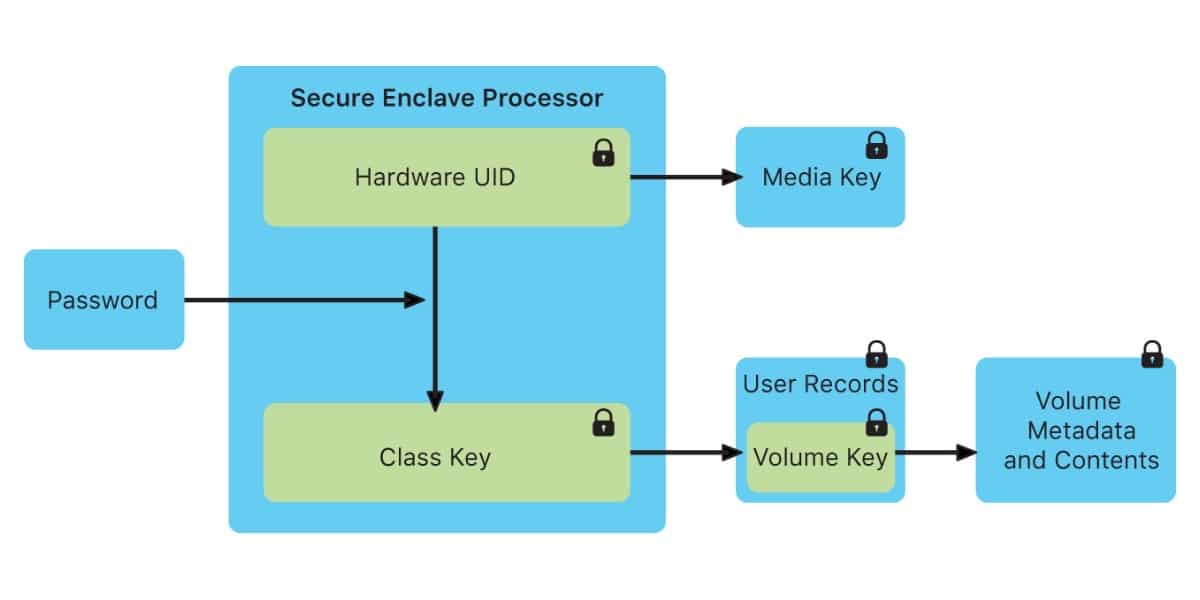
The Secure Enclave boots separately from the rest of the device. It runs its own microkernel, which is not directly accessible by your operating system or any program running on your device.
It is also responsible for store the keys it manages Sensitive data like passwords, your credit card used by Apple Pay, and even your biometric identification to enable Touch ID and Face ID. This makes it more difficult for hackers to gain access to your personal data without your password.
The expolit has no solution
The Team Pangu has found an "unpatchable" vulnerability on the Secure Enclave Processor (SEP) chip in iPhones. https://t.co/9oJYu3k8M4
- Jin Wook Kim (@wugeej) July 29, 2020
Now Pangu team members have found an exploit in Apple's Secure Enclave chip that could lead to breaking the encryption of private security keys. The bad thing is the vulnerability was found in the hardware and not in the software. So there is probably nothing Apple can do to fix it on devices that have already been shipped.
These are the devices that currently have the Secure Enclave chip:
- iPhone 5s and later versions
- iPad (5th generation) and later. Air, mini 2 and Pro.
- Computers Mac with T1 or T2 chip
- Apple TV HD (4th generation) and later
- Apple Watch Series 1 and later
- HomePod
Not everything is bad. Keep in mind that exploits like this usually require you to the hacker has physical access to the device in order to obtain any data, so it is unlikely that anyone will be able to access your device remotely.

Let's see if when you copy a piece of news, you copy it well, that not only do you not put the source, but to top it off you haven't even read it in full.