
It has been known that the iMac Pro, of which we will know more details as of tomorrow, the day of the launch, will have an Apple chip, designed to improve the security of certain Mac processes. We know the name of this new chip , which has been baptized as Apple T2, serves as a safe space for encrypted keys, intrusion in boot processes and control of the camera, audio and the hard disk itself. We know the details from the hand of Caleb sasser, co-founder of developer Panic. Apple debuted this system in the MacBook Pro, with the Apple T1 chip.
What Apple intends with this chip is isolate certain 'sensitive' information in a separate room from the rest of the system. In this way, accessing it is more complex than the rest of the system. Although the best known to the average user is the protection of sensitive information, such as passwords, this chip also encrypts hardware, as we learned from Sasser. He himself tweeted about it:
This new chip means that the storage encryption keys pass from the secure enclave to the on-chip hardware encryption engine: the key never leaves the chip ... and allows the verification of operating system, kernel, bootloader, firmware hardware. , etc. (This can be disabled)
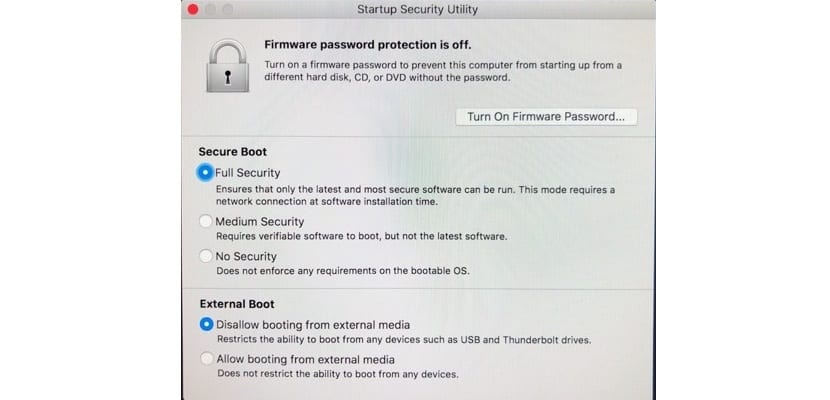
IMac Pro users can configure the actions of the Apple T chip to their liking2, in the preferences. In that case, users can set a firmware password, to prevent the Mac from starting from an external drive.
MacOs have new safe boot options. We have three scales: Full security, Medium security or disable security. If we activate full security, the system only runs the latest and safest software.
We can't wait to see each and every hidden feature of the new iMac Pro in the next few hours.