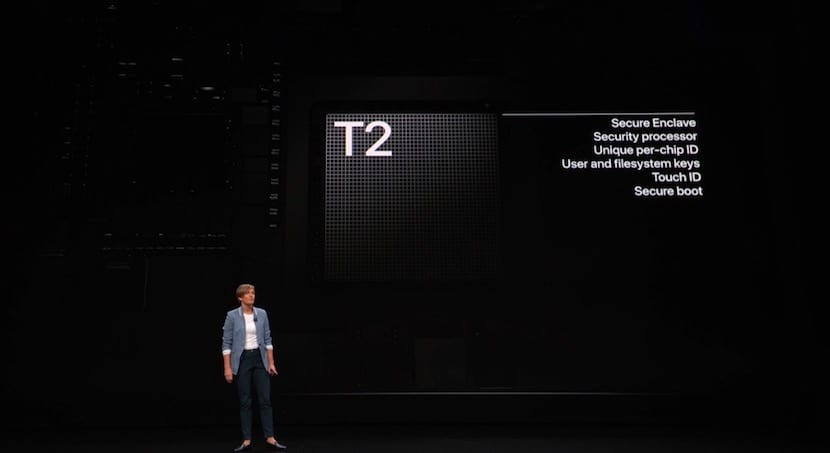
In the latest Apple models introduced in 2018, the MacBook Pro and MacBook Air, we have the T2 chip. This Chip is specially designed for mac security, to the point that some repairs carried out on these computers could be blocked when the Mac is programmed to block a possible attack.
The magazine The Verge has confirmed that, like the 2018 MacBook Pros, MacBook Airs would also be affected by repairs to their equipment, blocking the Motherboard and the ID sensor. What happens is that this happens in some repairs, and not in others.
If we check with Apple, the company does not go into details on the repaired Macs. We also do not know since when Apple is carrying out this measure. What is clear is that certain repairs can only be carried out at Apple or authorized dealers. Last month, iFixit was tampering with the 2018 Mac Book Pro with Touch Bar, and found no problem. Therefore, the repairs or equipment that cannot be performed outside of Apple and which are permitted are unknown.
El T2 chip It is specially designed to provide security to the Mac user, especially during login. Ensures the integrity of the system and hardware. The difference between a repair at Apple or authorized reseller and manipulation at another service is that Apple service validates the repair with the AST2 system, only available from Apple.
This validation software it is not available for download to the general public. Apple wants to ensure that the repairs of its equipment have a sufficient guarantee. In this way, when buying a second-hand Mac we can be sure that the repair has been carried out in an authorized center. The T2 Chip in turn controls the screen and the webcam, therefore repairing these components can have the same result as the motherboard or Touch ID.