Aspects such as ease of use, certain features and even the exterior design, in addition to the price, are decisive when purchasing one or another mobile phone, however in recent years, with the expansion of cloud services, the increase of tasks we carry out with our mobile devices or spy scandals, security has become a fundamental aspect to take into account when buying a new device. Sam Costello, iPhone and iPad expert, explains from About Technology the 5 reasons why iOS is more secure than Android, what do you think.
1 Market share
Although at first glance this reason seems somewhat out of tune, once we reflect on it it is entirely logical. Virus writers, hackers and cybercriminals want to have the greatest possible impact and this happens by attacking the most widespread platform, with the largest number of users. Android has the largest market share, around 80% compared to 20% for iOS and therefore is the number 1 target for hackers and criminals.
Costello further notes that “even if Android had the best security in the world, it would be virtually impossible for Google and its hardware partners to be able to close all security holes, fight all viruses, and stop every digital scam while still giving customers a useful device. "
2.Virus and malware
Given the above, the result is that "Android presents the most viruses, hacks, and malware":
According to a recent study, 97% of malware on smartphones is targeting Android. That is just mind blowing. Even more surprising, according to this study, is 0% of the malware they found targeting the iPhone. The last 3% pointed to the old, but widely used, Nokia Symbian platform, points out San Costello.

3.Sandboxing
This is a fundamental aspect for security because the way in which Apple and Google have designed their respective iOS and Android operating systems, and the way in which they allow applications to run, is very different and leads to very different security situations. .
Apple Lossless Audio CODEC (ALAC), uses a technique called sand boxing which basically means that each application runs in its own "closed" space, so the malware that can affect said app does not have to spread to the rest of the device; And although applications are increasingly communicating with each other, this sandboxing continues to be forced. "With this in mind, it's no surprise that hackers don't try to attack the iPhone too much."
For their part, Google and Android have chosen to prioritize maximum openness and flexibility, with great benefits for developers and users, “but it also means that the platform is more open to attacks. Even the head of Google's Android team admits that Android is less secure, saying:
"We cannot guarantee that Android is designed to be secure, the format was designed to give more freedom ... If I had a company dedicated to malicious software, I would also target Android."
4.App Review
The app stores of both platforms, Google Play and App Store they also play a fundamental role in this of security. Receiving a virus or attack hidden in an application is really possible on both platforms however, "it is much less likely to occur on the iPhone."
En App StoreApplications undergo a rigorous review process that can take days and even up to two weeks until it is finally approved and presented in the App Store, however in Google, the review process can take just a couple of hours. The result of this, as Sam Costello points out, is that “in 2013, the app store for Google Play had 42.000 applications on it, capable of stealing user information«While the cases in the App Store have been really exceptional.
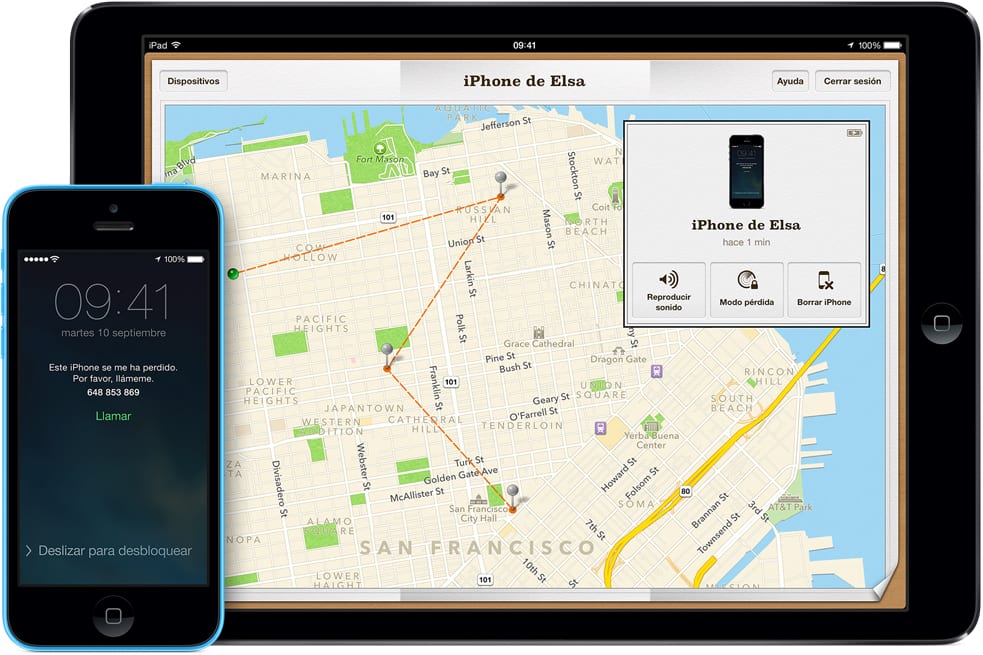
5.Find missing devices
The physical security of our mobile devices in case of loss or theft is also of vital importance. In this regard, Sam Costello points out the obvious:
For many years, iPhones were some of the most stolen devices in the US (a surprisingly high percentage of overall thefts in New York City were simply iPhones; in 2013 nearly 10.000 iPhones were stolen in New York City alone) . Apple has slashed those numbers with a combination of two features: Find my iPhone and Activation Lock. Find My iPhone is Apple's technology with GPS to locate the location of a stolen iPhone. It has been around since 2010. Activation Lock was introduced in 2013 and prevents thieves from doing anything with stolen phones unless they have the Apple ID that was used to activate the phone originally.
Google's answer to Find My iPhone, called Android Device Manager, debuted in the summer of 2013 and offers many of the same features - find the phone on a map, wipe data remotely, but it has nothing to deter from theft. such as Activation Lock.
[Divider]
Everything seen before is true, as Costello explains, however everything falls apart when we do jailbreak to our iDevice. The Jailbreak reverses the balance and puts us in exactly the same position as Android: greater flexibility to install and modify everything we want, in exchange for sacrificing security:
In the history of the iPhone there have been very, very few hacks and viruses, but the ones that have existed almost all have attacked jailbroken phones. Therefore, if you are considering jailbreaking your phone, keep in mind that it will make your device much less secure.
What do you think of this exhaustive comparative analysis between iOS security and Android security? Are you agree? Do you prefer security or flexibility? Do you think that one day both extremes will become compatible?
SOURCE: About Technology
