
When the use we make of Mail involves the sending of confidential information or that we may consider private enough as to be able to be read it is possible that the use of this tool is a good idea.
GPGTools is an open source project based on OpenPGP and will be integrated into the system's default Mail client to generate a key and thus encrypt the emails that we consider appropriate.
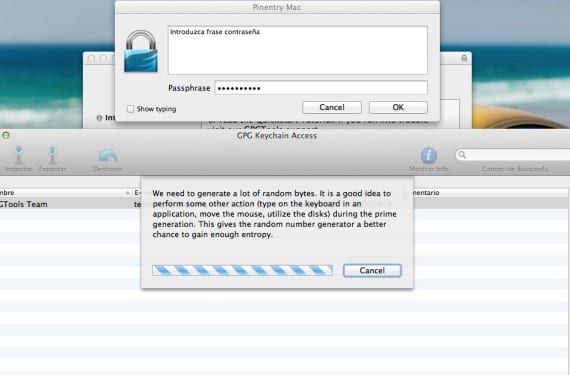
To begin we will have to go to the website of gpgtools to download the software and install it in a regular way, mount the image and launch the installer. Next we will go on to configure our key within the keychain of the «GPG Keychain Access» that we will associate each of our email addresses or we can modify to assign a different one per address.
Once this is done, when we go to write a new email we will be able to see how a menu will appear in the upper right corner to choose the encryption service and a padlock to encrypt the message along with a "check" box to enable / disable digital signature.
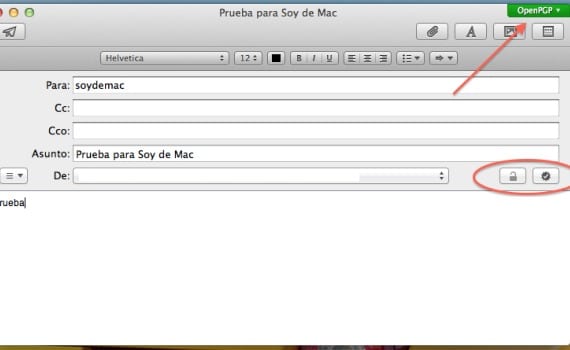
When the email is sent to the recipient, it will arrive in your inbox as an email with an attachment with the information contained in it, but in an illegible way, so that if you do not have GPGTools with the correct password, you will not be able to decrypt the message. at least quickly or easily so this becomes the great downside of this tool.
Even so, for a series of contacts where you know that they have GPGTools or similar, such as gpg4win on windows, it is a great option to protect your files.
More information - How to encrypt a PDF before sending it by Mail